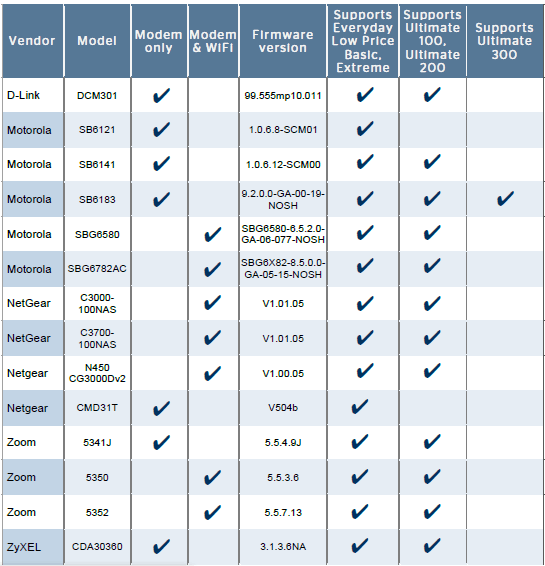
If you own or lease a Motorola/Arris SurfBoard 5100, 6121, or 6141 cable modem, security researchers have uncovered an annoying vulnerability that could expose you to a denial of service attack.
If you own or lease a Motorola/Arris SurfBoard 5100, 6121, or 6141 cable modem, security researchers have uncovered an annoying vulnerability that could expose you to a denial of service attack.
David Longenecker first discovered the flaw with the world’s most popular cable modem — the SB-6141, a highly recommended DOCSIS 3 model. The firmware does not password protect access to the cable modem’s configuration menu, accessible by visiting 192.168.100.1 in a web browser.
In addition to technical information about the modem and the cable system’s current cable broadband configuration, there are two user accessible reset buttons, one to reboot the modem and another to reset it to its original factory settings. Rebooting the modem will disrupt your Internet connection for under a minute, but doing a factory reset could bring the modem offline until someone reaches the cable company to request the modem be reauthorized. An individual with nefarious intent can repeatedly reset the modem, bringing the user offline again and again.
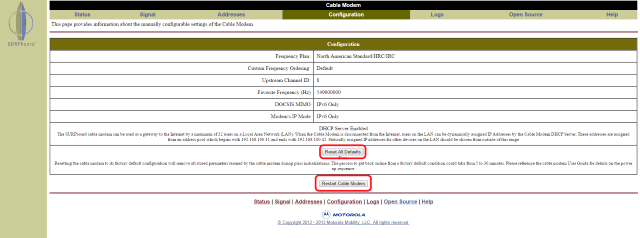

SB6141 is a DOCSIS 3 modem
The Houston Chronicle explains how this could become a widespread problem:
Included within this interface is the ability to reset the modem. A user can be tricked into clicking on a simple link that will reboot the SB6141, and you can see a proof of concept here. Note that if you have one of these modems with this flaw, and you click the link, your modem WILL reboot.
Normally, you’d have to be sitting at a computer on the same network as the modem to trigger a reboot. But the link above takes advantage of the fact that you can mask a local Web page address as an image file. As Longenecker describes it:
Did you know that a web browser doesn’t really care whether an “image” file is really an image? Causing a modem to reboot is as simple as including an “image” in any other webpage you might happen to open – which is exactly the approach taken on the RebootMyModem.net proof of concept:
<img src=”http://192.168.100.1/reset.htm”>
Of course it’s not a real image, but the web browser doesn’t know that until it requests the file from the modem IP address – which of course causes the modem to reboot. Imagine creating an advertisement with that line of code, and submitting it to a widely-used ad network…
Advanced users can go into their router’s configuration page and block access to the IP address 192.168.100.1 (the modem’s configuration page) for anyone inside their network. That step prevents you or anyone else on your network from accidentally clicking a link that tricks your modem into rebooting. But most users will probably wait until Arris has distributed firmware updates that cable operators will eventually apply to correct this vulnerability. The upgrade will occur in the background and most users will never notice it.


 Subscribe
Subscribe


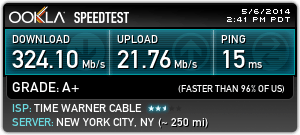 Time Warner Cable’s major broadband speed upgrade is alive in the Astoria, Woodside and Long Island City neighborhoods of Queens, N.Y.
Time Warner Cable’s major broadband speed upgrade is alive in the Astoria, Woodside and Long Island City neighborhoods of Queens, N.Y.