A prominent story airing last week on the NBC Nightly News with Brian Williams suggested visitors to the Sochi Olympic Games in Russia should expect their Android smartphone or laptop to be infiltrated by hackers moments after being switched on. A closer examination of the story suggests NBC News reporter Richard Engel had to go out of his way to get infected with malware.
[flv]http://www.phillipdampier.com/video/NBC News Hackers at the Olympics 2-4-14.flv[/flv]
Is it really too late to protect your electronic device if you power it on at the Sochi baggage claim facility at the airport, as NBC News’ Brian Williams claims? (3:35)
Trend Micro security expert Kyle Wilhoit, who helped design the experiment based on Engel’s usage habits, admitted security holes were left wide open on the tested devices:
On all of the devices, there was no security software of any type installed. These devices merely had standard operational programs such as Java, Flash, Adobe PDF Reader, Microsoft Office 2007, and a few additional productivity programs.
When considering this experiment, there were some basic things to be considered. First was mimicking the user behavior of Richard Engel. Since these were going to be machines with fake data, it was important to accurately imitate his normal activities. I had to investigate Richard’s user habits. In addition to other information, I needed to understand what he actually did on a daily basis, and sites he commonly visits. Also, I needed to understand where he posted. Did he post information on forums? Did he post on foreign language sites?
NBC’s story implied that three new devices, including an Apple MacBook Air, an Android phone, and a Lenovo laptop running Windows 7 were all hacked within minutes of being switched on for the first time, right out of their respective boxes.
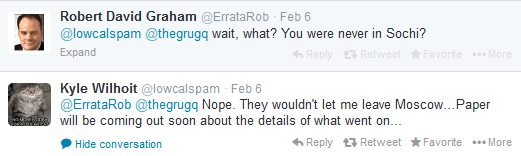
A story about hacking at the Olympics in Sochi, Russia was recorded largely in Moscow, more than 1,000 miles away.
Careful observers will notice Wilhoit is wandering around Moscow, more than 1,000 miles away from Sochi. Wilhoit would later clarify in a tweet he never visited Sochi at all. A closer look at shots of computer screens show the reporter clicking on suspicious links and visiting obviously phony Olympics-oriented websites. With no virus or malware protection and Engel’s apparent willingness to click on anything suggests you should never loan him your laptop or phone.
NBC News went over the top getting their Android phone hacked. In fact, Engel not only had to manually find and download the infected app that let the hackers in, he had to navigate a set of menus to disable Android’s built-in security, turning on permission to download apps from unknown or third-party websites not affiliated with the Google Play store. Installing a security-compromised app also brings multiple additional warning messages advising users not to proceed. Under these circumstances, Aunt Sue can rest easy her Galaxy S4 is not accidentally open season for hackers while she watches the downhill skiing events.
Media sensationalism makes for good ratings but requires a lot of truth dodging to make the story real. This is an example.


 Subscribe
Subscribe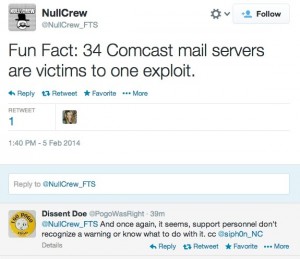 At least 34 of Comcast’s email servers have been compromised by a well-known hacker group that posted evidence, the exploit, and certain administrative passwords online to embarrass the company and expose its poor security practices.
At least 34 of Comcast’s email servers have been compromised by a well-known hacker group that posted evidence, the exploit, and certain administrative passwords online to embarrass the company and expose its poor security practices.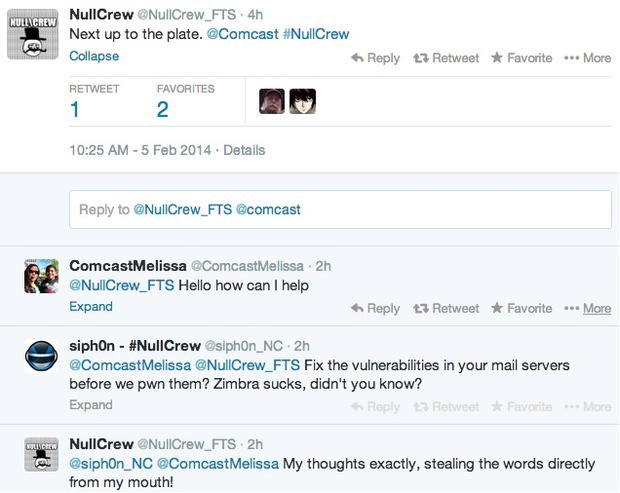
 Hackers exploited poor coding practices at an Ottawa-based third-party contractor to access and eventually publish more than 20,000 usernames and passwords of Bell Canada’s small business customers on a website.
Hackers exploited poor coding practices at an Ottawa-based third-party contractor to access and eventually publish more than 20,000 usernames and passwords of Bell Canada’s small business customers on a website. Trustwave Holdings, a security company based in Chicago, Ill., said in a 2013 report that poor coding practices have made the SQL injection attack a threat for more than 15 years.
Trustwave Holdings, a security company based in Chicago, Ill., said in a 2013 report that poor coding practices have made the SQL injection attack a threat for more than 15 years. AT&T’s investment in U-verse expansion is expected to peak this year as part of its “Project VIP” effort to bring the fiber to the neighborhood service to more areas and offer faster broadband speeds to current customers.
AT&T’s investment in U-verse expansion is expected to peak this year as part of its “Project VIP” effort to bring the fiber to the neighborhood service to more areas and offer faster broadband speeds to current customers.