
KMGH Denver reporter Marshall Zelinger holds up some of the 50 emails received in the newsroom from victims that had new iPhone 6 smartphones billed to their Verizon Wireless account in February. (Image: KMGH-TV/Denver)
If you want a new iPhone 6 and don’t want to bother paying for it, buy one from an Apple store and they just might bill your purchase to a unknowing third-party with few or no questions asked.
The scam, which first emerged last month, has now spread coast to coast and now involves more than 100 illegally obtained iPhones that victims complain were billed to them with little or no verification by Apple or wireless carriers. Many of those orders, but not all, originated inside Apple retail outlets and AT&T told one Connecticut victim they are being hampered in their fraud investigation by Apple, which is allegedly not cooperating with the wireless carrier.
In Denver, dozens of victims shared their stories with KMGH-TV back in February when the fraud first appeared.
“We have heard from more than 50 customers who said their accounts have been charged for new iPhone 6s, and new service plans or altered service plans, that they never requested,” reporters told viewers.
Verizon Wireless and their customers were the original targets, and Verizon initially blamed their own customers for the fraud.
Denver area resident Terri Olson was livid after Verizon accused her son of ordering new iPhones on her business account.
“He happened to be in the office that day,” said Olson. “We’re like, ‘Wow, he’s here. He’s not on the phone with Verizon.'”
Verizon promised it would drop the charges and tighten security on her account, but two days later, Verizon called confirming they had just accepted and shipped an order for four new iPads.
“She explained to me that she had my son on the other phone line, on hold. Funny thing, he was here with me,” Olson told KMGH. “We proceed, later that day, to get an email confirmation from Verizon that our order is shipping to Henderson, Nevada — (the order) that was supposedly stopped.”
Olson was able to get FedEx confirmation the four iPads were indeed sent to Henderson and signed for by someone, and it was not her son.
“It’s no way to run a business. If I did this to my customers, oh my God, we’d be out of business,” said Olson.
A few days later, more than $2,000 in fraudulent charges showed up on her Verizon bill, and the company was stalling on crediting her account.
“Basically, I’m risking my entire fleet of cell phones and data plans and iPads and everything because I don’t want to pay thousands of dollars ahead, waiting for this supposed credit,” said Olson. “I have already gone up the food chain. I’ll continue to go up the food change. We’re not taking no for an answer.”
Another Denver victim suddenly received news he was the proud new owner of four new iPhone 6 smartphones from Verizon Wireless, despite the fact he was an AT&T customer and had never authorized the purchase of the phones or the two-year contracts that came with them. A Verizon store told him if he didn’t return the phones, he’d be on the hook for their full value — $449 each as well as $160 in service charges.
[flv]http://www.phillipdampier.com/video/KMGH Denver More than 50 Verizon customers tell 7NEWS they are victims of unauthorized charges on their accounts 2-10-15.mp4[/flv]
In February, KMGH in Denver reported more than 50 viewers were billed for illegally obtained Apple iPhones charged to their Verizon Wireless accounts. (2:35)
Verizon couldn’t believe the security problem was on their end or at their authorized resellers, so they initially blamed customers in a statement:
As we have stated before, there is no evidence of a data breach at Verizon Wireless that would put our customers’ information at risk. In order for us to look into this further, we will need to work with our customers one-on-one.
In fraud cases, we often find customers have been tricked or persuaded to provide information that allows fraudsters to compromise their accounts. But without the further information you have offered to provide on these particular cases, we cannot determine what has happened.
That triggered a social media backlash.
“For them to suggest that this was phishing and effectively blame the customer is even more appalling,” wrote one victim. “I realize phishing happens too and folks are duped, but that is not the way this happened in my case.”
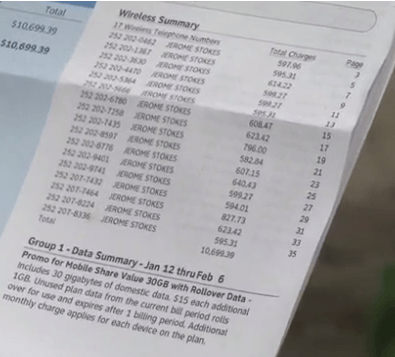
A North Carolina church was billed for 17 illegally-obtained iPhone 6 smartphones, totaling more than $10,000. (Image: WAVY-TV/Norfolk)
Verizon Wireless has been the victim of phishing attempts inviting customers to use their Verizon Wireless login credentials and a four digit billing code which many might assume to be the last four digits of their Social Security number to get a one-time credit on their account. The link actually leads to a fraudulent website, where information obtained by the hacker could be used to log into a legitimate customer’s Verizon Wireless account. But a Verizon store representative tells Stop the Cap! that alone would not be enough to complete a purchase at a retail store.
“A phishing fraud victim would be providing the crook login information that could be used to order equipment off Verizon’s website, which seems to be a lot less risky than walking into a retail store to commit fraud,” a Verizon store employee not authorized to speak to the media tells Stop the Cap! “Verizon confirms direct online orders right away with customers, so they would know immediately if there was something wrong with their account. They wouldn’t usually know if a third-party retail reseller billed a phone to their account until the bill or the phone came.”
After the number of fraud reports ballooned, Verizon Wireless evidently tightened its own internal security because by late February, the fraudsters moved on to AT&T.
In Hartford, Conn., Meg O’Brien found out she was a victim when her own phones stopped working.
“Three of our four phones had no service,” O’Brien told Hartford’s WFSB-TV. When she called AT&T, they knew straight away what was happening. “They responded by saying ‘oh – hold on a minute – there’s obviously some fraud…you have three new iPhone 6’s’ and I said ‘ah no we have no iPhone 6’s’.”
AT&T told O’Brien she was far and away not the only victim, and AT&T was concerned because Apple reportedly was not cooperative assisting AT&T in tracking down the Apple retail store(s) where the theft originated. AT&T did confirm the thieves were able to acquire the equipment by charging it to random AT&T wireless accounts.
The Apple store(s) involved allegedly did not need proof of identity or a credit card to complete the transactions, and that leaves O’Brien fuming.
She told WFSB she found it unbelievable Apple stores were handing out phones to customers with nothing more than an AT&T customer’s phone number, and she’s unhappy Apple isn’t being forthcoming.
“So I have no idea what other information has been sold or bought or anything,” O’Brien said. She is filing a complaint with Connecticut’s attorney general.
An Apple spokesperson tells us nobody is supposed to be able to walk out of an Apple store with a new phone without a complete wireless account number, the last four digits of the account holder’s Social Security number, photo ID, and final approval from a wireless carrier. Apple claims the purchase met all four criteria, something O’Brien disputes.
[flv]http://www.phillipdampier.com/video/WFSB Hartford Hacker charged 6 iPhones to woman ATT account 3-11-15.mp4[/flv]
WFSB in Hartford reports AT&T customer Meg O’Brien was victimized by fraudulent purchases at an Apple retail store Apple is refusing to name. (2:39)
The Fountain of Life Ministries in Elizabeth City, N.C., has been victimized at least twice by a crook using the church’s name to get at least 17 iPhone 6 smartphones for himself, leaving the church with the bill from AT&T.
 Church employees first learned they were targets when the thief tried to acquire the phones from Verizon Wireless, which apparently learned its lesson from earlier fraud cases and rejected the purchase.
Church employees first learned they were targets when the thief tried to acquire the phones from Verizon Wireless, which apparently learned its lesson from earlier fraud cases and rejected the purchase.
AT&T was more receptive, authorizing the purchase of more than a dozen phones bought on different days.
“I’m just amazed somebody would do that,” Pastor Preston Pitchford told WAVY-TV.
Church employee Christy Wells was even more stunned when the bill arrived.
“When I saw it was from AT&T, I was like, I know this has got to be him. He probably succeeded,” Wells told WAVY. “I see a charge to Fountain of Life for $10,000, and I knew that wasn’t for us. Who would even think to do something like this?”
The church doesn’t use iPhones and doesn’t have an account with AT&T.
[flv]http://www.phillipdampier.com/video/WAVY Norfolk Church billed 10K for fraudulent iPhone purchases 3-3-15.flv[/flv]
The Fountain of Life Ministries in Elizabeth City, N.C. was victimized twice by iPhone 6 fraud. Verizon Wireless rejected the fraudster’s first attempt, but AT&T accepted his second… for 17 iPhones. From WAVY-TV in Portsmouth, Va. (2:12)



 Subscribe
Subscribe



 A security flaw exposed the personal data of millions of Charter Communications customers nationwide, including payment details, account holders’ names and addresses, and specifics about the equipment used to receive Charter service.
A security flaw exposed the personal data of millions of Charter Communications customers nationwide, including payment details, account holders’ names and addresses, and specifics about the equipment used to receive Charter service. “The vast majority of Charter customers use a version of the site on which this security vulnerability was not an issue,” a company spokesperson explained, noting the number of customers affected was less than one million. The company is auditing its systems, he said, and has so far “seen no evidence of any password or data hacks.” The exposed data did not include credit card numbers.
“The vast majority of Charter customers use a version of the site on which this security vulnerability was not an issue,” a company spokesperson explained, noting the number of customers affected was less than one million. The company is auditing its systems, he said, and has so far “seen no evidence of any password or data hacks.” The exposed data did not include credit card numbers.


 Church employees first learned they were targets when the thief tried to acquire the phones from Verizon Wireless, which apparently learned its lesson from earlier fraud cases and rejected the purchase.
Church employees first learned they were targets when the thief tried to acquire the phones from Verizon Wireless, which apparently learned its lesson from earlier fraud cases and rejected the purchase.