
Perhaps not for long.
Time Warner Cable customers who spent hundreds or thousands of dollars in security equipment and add-ons may be left with nothing but their 18-month contract as Charter Communications considers pulling the plug on Time Warner’s IntelligentHome security service.
DSL Reports appears to have the exclusive story this morning that insiders familiar with the company’s business operations are claiming IntelligentHome may be one of the first casualties of the giant merger between Charter, Time Warner Cable, and Bright House.
As Stop the Cap! reported earlier this morning, Charter executives are performing a top-to-bottom analysis looking to wring cost savings out of the merger deal. The result will likely be the elimination of anything seen as duplicating Charter Spectrum’s own suite of products and services or going beyond Charter’s philosophy of focusing on “core services.” That could be bad news for Time Warner Cable employees managing or supporting non-conforming services as well, and at least some could be headed for the unemployment office.
A strong clue the days of IntelligentHome may be numbered is word employees are now supposed to keep it a secret:
While the source states that no formal shutdown of the service has been announced, sales and service employees are being told to no longer mention the service in call conversations or presentations with customers. The source also states that “rumblings by managers” suggests the service may not be long for this world.
Should Time Warner Cable shutter the service, the insider states that could be trouble for the customers that recently shelled out significant amounts of money for IntelligentHome hardware.
“What is particularly concerning is that many customers are in 18 month contracts and have purchased hundreds or even thousands of dollars in equipment,” states the insider.
 If Time Warner does shutter the service, customers will likely be released from their contracts penalty-free, but they may also be stuck with useless equipment they can’t use with another alarm system.
If Time Warner does shutter the service, customers will likely be released from their contracts penalty-free, but they may also be stuck with useless equipment they can’t use with another alarm system.
Cable operators have dabbled in the home security business since the 1970s, but many early attempts were scrapped after waves of consolidation orphaned a variety of incompatible technologies with new owners that had little interest in maintaining the service. The insatiable quest for higher Average Revenue Per User (ARPU) has pushed the cable industry to find more ancillary services that could boost cable bills and keep Wall Street happy. They tried music services like Music Choice and DMX, home video game services, broadband for telecommuters, and eventually returned to home security.
Time Warner Cable first launched IntelligentHome in 2011. It immediately threatened traditional home security services from companies like ADT because IntelligentHome could manage easy remote access to control home security settings, lighting, and thermostats from a computer, tablet, or smartphone. Customers upgrading to a video-capable system could even stream camera video over the Internet through a live feed. A tablet-like touchscreen control enhanced the experience with access to current weather, news, and traffic.
Icontrol manages the software platform that powers Time Warner’s IntelligentHome, along with home security services offered by a number of other cable operators.
Time Warner Cable did not develop IntelligentHome exclusively in-house. Most large cable operators rely on connected home security system software solutions powered by a platform developed by Icontrol.
 Charter Communications is one of only a few cable companies that have shown no interest in selling home security services (Cablevision is another). In 2013, it dismissed any interest in getting into the business, telling Reuters it preferred to concentrate on its “core business.” Nothing seems to have changed. As of this year, the only security protection Charter offers customers is antivirus software for their computers.
Charter Communications is one of only a few cable companies that have shown no interest in selling home security services (Cablevision is another). In 2013, it dismissed any interest in getting into the business, telling Reuters it preferred to concentrate on its “core business.” Nothing seems to have changed. As of this year, the only security protection Charter offers customers is antivirus software for their computers.
An exit from IntelligentHome could also have a major impact on Time Warner Cable’s owned-and-operated CSAA 5-Diamond Rated Emergency Response Center, which answers when it detects a break-in or when a customer hits a panic button.
Most estimates put the number of customers paying for IntelligentHome at less than 100,000 nationwide, but that select group is likely to have a substantial buy-in to the service and would definitely feel its loss.
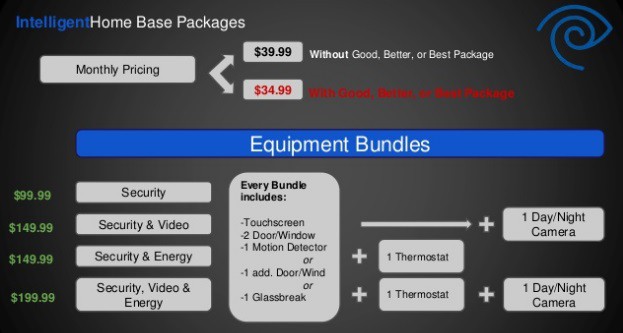
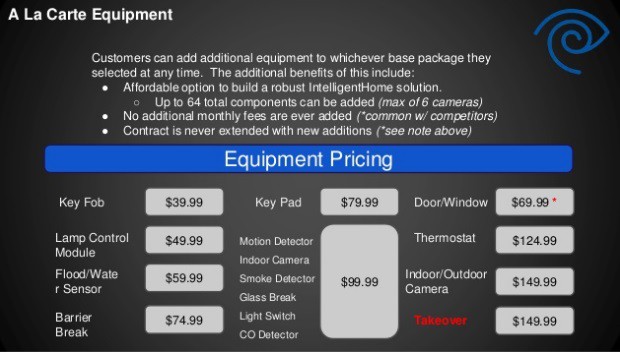
Although Time Warner Cable advertises IntelligentHome at prices starting between $35-40 a month, that doesn’t afford much protection. Customer can choose between packages of different equipment bundles that range from $99.99 to $199.99. A la carte equipment is also available. A very basic entry-level system packages a tablet-like controller with protection for only two doors or windows and one motion detector. That might be suitable for an apartment, but homeowners often upgrade to cover more potential entry points. As a result, IntelligentHome has proven a tough sell for customers already confronted by cable bills that often approach or exceed $200 a month, before the alarm service is added.
Time Warner has attempted to change the marketing of IntelligentHome to emphasize more of its home automation and monitoring features, and routinely offers a $200 gift card to entice new customers. But it may not have worked enough to interest Charter, which shows every sign it wants to simplify the cable bundle, not clutter it up with extras. The insider told DSL Reports he hoped Charter would find a way to manage existing customers and not abandon them should the service be discontinued. If not, tens of thousands of Charter customers will have bought a lot of equipment with nothing to show for it.
DSL Reports stresses no final decision has been made.


 Subscribe
Subscribe If you own or lease a Motorola/Arris SurfBoard 5100, 6121, or 6141 cable modem, security researchers have uncovered an annoying vulnerability that could expose you to a denial of service attack.
If you own or lease a Motorola/Arris SurfBoard 5100, 6121, or 6141 cable modem, security researchers have uncovered an annoying vulnerability that could expose you to a denial of service attack.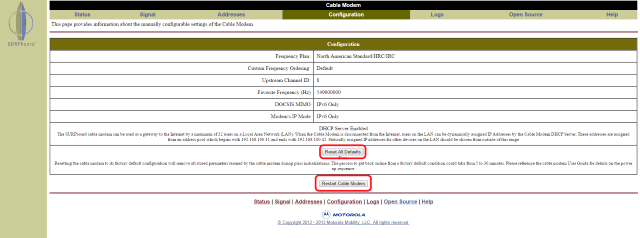



 Less than a week after ISIS-connected terrorists is Paris allegedly killed at least 129 people in a coordinated attack, false reports continue to be spread through news services and social media. It’s enough to make you cringe.
Less than a week after ISIS-connected terrorists is Paris allegedly killed at least 129 people in a coordinated attack, false reports continue to be spread through news services and social media. It’s enough to make you cringe.

 While the online world is beefing up security systems with encryption and two-factor authentication to keep the hackers out, Frontier Communications’ e-mail password system harkens back to an earlier, innocent era when passwords were stored as plain text in a database practically anyone could access.
While the online world is beefing up security systems with encryption and two-factor authentication to keep the hackers out, Frontier Communications’ e-mail password system harkens back to an earlier, innocent era when passwords were stored as plain text in a database practically anyone could access.
 Silverman’s password was easy to find because Frontier is storing that information in plain text format, a potentially enormous security risk. Security experts say storing passwords in a plain text format, even if access is limited to customer service representatives, make them vulnerable to hacking. A single disgruntled employee or unknown security hole in a Frontier support center could theoretically expose millions of Frontier customers to password theft. The fact Frontier also e-mails transcripts of customer chat sessions to customers also represents a potential security risk. In Silverman’s case, Frontier helpfully obscured his account number, but not his password.
Silverman’s password was easy to find because Frontier is storing that information in plain text format, a potentially enormous security risk. Security experts say storing passwords in a plain text format, even if access is limited to customer service representatives, make them vulnerable to hacking. A single disgruntled employee or unknown security hole in a Frontier support center could theoretically expose millions of Frontier customers to password theft. The fact Frontier also e-mails transcripts of customer chat sessions to customers also represents a potential security risk. In Silverman’s case, Frontier helpfully obscured his account number, but not his password.