ARRIS, one of the country’s largest suppliers of cable modems, is under scrutiny after a security researcher discovered not one, but two secret “backdoors” potentially affecting more than 600,000 of the company’s installed cable modems/home gateways that could allow hackers access to a customer’s equipment and home network.
ARRIS, one of the country’s largest suppliers of cable modems, is under scrutiny after a security researcher discovered not one, but two secret “backdoors” potentially affecting more than 600,000 of the company’s installed cable modems/home gateways that could allow hackers access to a customer’s equipment and home network.
Bernardo Rodrigues published a report of the exploits on his blog, which affect ARRIS cable modem models including TG862A, TG862G, and DG860A. Rodrigues reports only ARRIS and your local cable company can fix the security problems, and neither seem to be in much of a hurry.

The ARRIS Touchstone 860, which can be identified by its model number depicted on the front lower right of the modem.
“Securing cable modems is more difficult than other embedded devices because, on most cases, you can’t choose your own device/firmware and software updates are almost entirely controlled by your ISP,” Rodrigues writes. Indeed, very few cable modems allow users to self-update their equipment with the latest firmware. To guarantee uniformity, that privilege is given exclusively to the cable company providing service, even if a customer owns their own modem outright.
“ARRIS SOHO-grade cable modems contain an undocumented library (libarris_password.so) that acts as a backdoor, allowing privileged logins using a custom password,” Rodrigues writes. “The backdoor account can be used to enable Telnet and SSH remotely via the hidden HTTP Administrative interface “http://192.168.100.1/cgi-bin/tech_support_cgi” or via custom SNMP MIBs.”
While exploring the potential security damage that backdoor could permit, Rodrigues stumbled on a second, open to additional exploitation by hackers.
“The undocumented backdoor password is based on the last five digits from the modem’s serial number,” Rodrigues wrote. “You get a full busybox shell when you log on the Telnet/SSH session using these passwords.”

ARRIS TG862
In plainer language, one or both backdoors will allow a hacker to bypass the modem’s usual security protections and provide the intruder with full remote access to the affected cable modem. Hackers have likely already identified the security lapse and have exploited it, with some suspecting access key generators are already available allowing the user to automate attempts to reach affected modems on a significant scale.
Unfortunately for consumers, neither ARRIS or cable operators appear to be rushing to update the affected firmware to eliminate the backdoors, having waited more than two months just to acknowledge Rodrigues’ report.
For now, customers using these devices exclusively as cable modems are least likely to suffer a serious security lapse. More at risk are consumers relying on these three models as both a cable modem and home gateway providing Wi-Fi access around the home. Theoretically, hackers could use one or both exploits to gain access to your home network. Consumers using one of the affected models should contact their local cable company and ask them to replace the device with an alternative, preferably from a different manufacturer.
At least one cable company reported they are working with ARRIS to correct the flawed firmware, but early efforts have not been successful. It may be prudent for some security-conscious customers not to wait.


 Subscribe
Subscribe

 While the online world is beefing up security systems with encryption and two-factor authentication to keep the hackers out, Frontier Communications’ e-mail password system harkens back to an earlier, innocent era when passwords were stored as plain text in a database practically anyone could access.
While the online world is beefing up security systems with encryption and two-factor authentication to keep the hackers out, Frontier Communications’ e-mail password system harkens back to an earlier, innocent era when passwords were stored as plain text in a database practically anyone could access.
 Silverman’s password was easy to find because Frontier is storing that information in plain text format, a potentially enormous security risk. Security experts say storing passwords in a plain text format, even if access is limited to customer service representatives, make them vulnerable to hacking. A single disgruntled employee or unknown security hole in a Frontier support center could theoretically expose millions of Frontier customers to password theft. The fact Frontier also e-mails transcripts of customer chat sessions to customers also represents a potential security risk. In Silverman’s case, Frontier helpfully obscured his account number, but not his password.
Silverman’s password was easy to find because Frontier is storing that information in plain text format, a potentially enormous security risk. Security experts say storing passwords in a plain text format, even if access is limited to customer service representatives, make them vulnerable to hacking. A single disgruntled employee or unknown security hole in a Frontier support center could theoretically expose millions of Frontier customers to password theft. The fact Frontier also e-mails transcripts of customer chat sessions to customers also represents a potential security risk. In Silverman’s case, Frontier helpfully obscured his account number, but not his password.
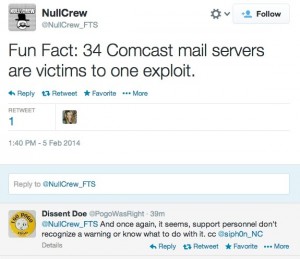 At least 34 of Comcast’s email servers have been compromised by a well-known hacker group that posted evidence, the exploit, and certain administrative passwords online to embarrass the company and expose its poor security practices.
At least 34 of Comcast’s email servers have been compromised by a well-known hacker group that posted evidence, the exploit, and certain administrative passwords online to embarrass the company and expose its poor security practices.