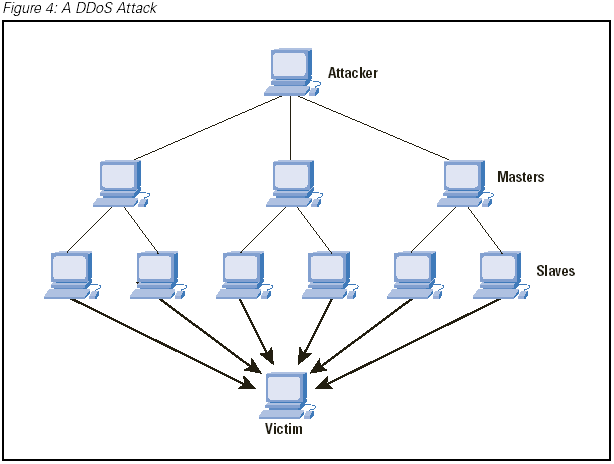
A denial of service attack often directs compromised computers to join in the attack, bringing an enormous amount of simultaneous traffic to a single, targeted user. The result is usually very slow or no Internet service. (Image courtesy: Cisco)
For nearly a month, Verizon FiOS customers in Westborough and Northborough, Mass. have experienced frequent slowdowns and outages of their Internet and telephone service that Verizon now admits have been traced to a denial-of-service attack on a single residential customer in Westborough.
“Someone deliberately flooded that customer with an overwhelming amount of traffic that rendered their Internet service inoperable,” Verizon spokesman Philip G. Santoro told The Telegram. “When that happened, it caused Internet service to periodically slow down for other customers in Westborough,” he wrote. “We are working to restore service to normal as soon as possible. DOS attacks are all too common today among customers of all Internet providers. It’s important to remind Internet users to keep their firewalls operating and to keep their security software current.”
When the newspaper first reached Santoro for comment, he claimed there wwere no widespread outages reported, but angry customers disagreed on the community’s Facebook page and six filed complaints with the state’s Office of Consumer Affairs and Business Regulation.
The outages have been a problem as far back as Feb. 26, growing more frequent in number since March 3. Business customers were also affected.
“It happened around 3 o’clock, every day,” said Allen Falcon, chief executive officer for Cumulus Global, a cloud computing company in Westborough. “Sometimes it was a few minutes, sometimes 45 minutes to an hour.” A few times, the interruptions occurred in the morning, just after 9 a.m., he said.
 When the attacks began, they not only affected the company’s Internet connection, but also its business phone service.
When the attacks began, they not only affected the company’s Internet connection, but also its business phone service.
Verizon’s first solution was to replace FiOS routers, which proved ineffective.
Customer Steve Winer from Westborough told the newspaper sending Verizon crews out with new equipment was a waste of time and money.
“I am just wondering how much time and money was wasted on this,” he wrote the newspaper in an email. “I know I spent at least a couple of hours on the phone, and others shared similar stories. But, if you add up all the shipped routers and unnecessary service calls, along with the time both of us customers and (Verizon) personnel, I am sure it really adds up, and could have been avoided if someone had simply put two and two together and posted a chronic outage which began in February.”

Last week, Verizon finally identified the specific customer targeted by the cyber-attack and terminated his FiOS account, which also put an end to the service-disrupting attacks.
Some customers are wondering whether Verizon has an effective plan to deal with future cyber attacks.
“It seems FiOS is very vulnerable to these attacks, which not only affects the target’s service, but that of everyone else in town,” wrote Stop the Cap! reader Steve Read, a Northborough resident. “They need a way to quickly isolate these kinds of attacks and keep them from affecting other customers’ service.”
Customers affected by the outages can contact Verizon FiOS customer service and request credit for the outages.


 Subscribe
Subscribe
I’m wondering how it is an effective/reasonable defense to cut off the victim’s service? I’m hoping that what is being left unsaid here is that they somehow hooked him up with a new account, new IP, whatever.
In a datacenter the target IP would have been null routed within 24hrs, and there’s not even a need for notice in the case of a home user’s IP.
There’s no reason they couldn’t do what you’re asking, and give the user a new DHCP address but monitor to make sure it isn’t found and attacked again.
It’s strange given the amount of infrastructure and investment they have there’s no mention of anti-DDOS equipment in place.
Agreed. If just one attack can impact two towns’ worth of customers. that is a major vulnerability.