
Bad clutter.
How would you like it if a banner ad was inserted on the bottom of every web page, on top of content you are trying to read and eating away at your usage allowance?
Customers of CMA Communications can tell you, because their web browsing experience now includes advertising messages injected by the cable company to earn more revenue.
CMA, which operates rural cable systems in Texas, Louisiana, Mississippi and Nevada, provides up to 7/1Mbps service with a usage cap of 250GB they borrowed from Comcast.
Zachary Henkel discovered the rude intrusion last month when he navigated to Apple’s website and discovered an intrusive banner ad for H&R Block.
Tired from the day’s events and travel, I had planned to quickly look up the specifications of a Mac Mini, respond to a few emails and then get some sleep. But as Apple.com rendered in my browser, I realized I was in for a long night. What I saw was something that would make both designers and computer programmers wince with great displeasure. At the bottom of the carefully designed white and grey webpage, appeared a bright neon green banner advertisement proclaiming: “File For Free Online, H&R Block”. I quickly deduced that either Apple had entered in to the worst cross-promotional deal ever, or my computer was infected with some type of malware. Unfortunately, I would soon discover there was a third possibility, something much worse.
[…] It was apparent at this point, that my parent’s ISP, CMA Communications, had started injecting advertisements into websites requested by their customers. I felt dissatisfied to say the least. […] You might not be surprised to know that CMA Communications won’t confirm or deny that they are injecting advertisements into their customer’s web traffic.
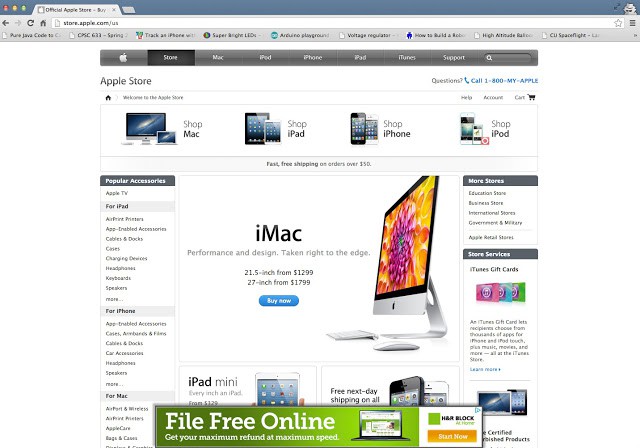
Customers of CMA Communications see this when they visit apple.com.
CMA Communications is using JavaScript code injection that overlays third-party advertisements on top of various websites, opening the door to subscriber irritation and some obvious conflicts. In fact, visitors to CMA’s own website could find themselves staring at advertising for CenturyLink, AT&T, or a satellite competitor, unless CMA specifically opts its own website out of the third-party ads.
Amazon.com features an ad with Flo from Progressive Insurance, LinkedIn links to a Verizon 4G phone ad, and Bing’s home page pitches AT&T phones. Henkel wants customers to complain, but the affected websites may be in the best place to stop the ad injections by threatening lawsuits against the cable company.


 Subscribe
Subscribe
Or the websites could switch to using SSL for all connections, preventing content injection and rendering the provider’s money-grabbing tactics (as well as any deep packet inspection!) moot.
(I’m in the process of doing so for my paltry little domain, too.)
I’d be semi-fine with this as long as it was opt-in, and I received a big discount for participating. This kind of crap really doesn’t fly unless it’s packaged with “free” wifi at merchant locations. Also, I’d demand either unlimited bandwidth (who knows how big the embedded applets in these ads are?) or some confirmed method to keep the ads from being counted toward any limit I suffered.
Yeah, you may be ok with it but websites like Google, Amazon, and Apple will not. CMA is not only injecting ads where there normally would not be any, but they are also overlapping ads that were originally in place.
This is not ok..
I’m pretty sure the courts will rule against this ad injection, as there is relative precedent, unless the payola is big enough. I recall a few years back that there was an absolutely voluntary, opt-in community, using a browser plug-in, which shared tags/comments which they placed on various websites. Other members of the community would see these tags when they visited the same websites. It was like a commenting system which was out of the hands of the website where the comments were being left. And commercial websites hated it with a burning vengeance. The websites weren’t actually being modified… Read more »
I just use Ad Block Plus to prevent this sort of thing.
It has been stated that Ad Block is not able to prevent this.
According to other users on reddit who are subjected to this, the only way to block it is to harvest and block the IP that the injected content is served from at the router level.
Ad Block could be updated to block this easily. Ad Block works by examining the web page source which is received, recognizing components, and modifying it to eliminate unwanted elements. Basically the reverse of the ad-injection. Ad code is going to be conspicuous. Obfuscated ad code will still be conspicuous. The bottom line is that the ad code cannot hide from Ad Block. You’ll still download the code script, though not the graphics and embedded applets it calls in turn. These scripts will be removed before your browser takes over and displays what is left. The ad injection would have… Read more »
Does the ad content (esp. videos) count against the user’s data cap?
Yep.
Well boo on that!
More than the cap issue, it’s the gall, the sheer impertinence and the sense of entitlement required to routinely interfere with and, indeed, alter the nature of a communication between your customers, and a third party. If I were to call Apple on the telephone, it wouldn’t be acceptable for my call to be interrupted by a robotic voice telling me that my discussion was being sponsored by H&R Block. So why do these companies feel that it’s in any way acceptable to alter the content of a web session in the same manner? On top of all of that,… Read more »