 AT&T has made it a whole lot easier to learn who has bought Apple’s transformative iPad. An AT&T security lapse permitted a third party to access and obtain the e-mail addresses and individual iPad ID’s of all 114,000 current owners of the device. That third party, Goatse Security, then promptly handed over the entire list — some 2,000 pages long, to Gawker — who exposed some big name iPad owners last week.
AT&T has made it a whole lot easier to learn who has bought Apple’s transformative iPad. An AT&T security lapse permitted a third party to access and obtain the e-mail addresses and individual iPad ID’s of all 114,000 current owners of the device. That third party, Goatse Security, then promptly handed over the entire list — some 2,000 pages long, to Gawker — who exposed some big name iPad owners last week.
More importantly, several high officials in government and the military were also identified as iPad owners, even as the security lapse could have given access to the exact location of any of them.
In the media and entertainment industries, affected accounts belonged to top executives at the New York Times Company, Dow Jones, Condé Nast, Viacom, Time Warner, News Corporation, HBO and Hearst.
Within the tech industry, accounts were compromised at Google, Amazon, Microsoft and AOL, among others. In finance, accounts belonged to companies from Goldman Sachs to JP Morgan to Citigroup to Morgan Stanley, along with dozens of venture capital and private equity firms.
Some of the movers and shakers exposed (Image: Gawker) In government, affected accounts included a GMail user who appears to be Rahm Emanuel and staffers in the Senate, House of Representatives, Department of Justice, NASA, Department of Homeland Security, FAA, FCC, and National Institute of Health, among others. Dozens of employees of the federal court system also appeared on the list.
While Gawker considers the implications of a widespread security breach and whether Apple or AT&T is to blame, others are focusing more intently on AT&T’s role in the misadventure.
AT&T e-mailed every iPad owner notification of the security breach only after it became public news:
“On June 7 we learned that unauthorized computer ‘hackers’ maliciously exploited a function designed to make your iPad log-in process faster by pre-populating an AT&T authentication page with the email address you used to register your iPad for 3G service. The self-described hackers wrote software code to randomly generate numbers that mimicked serial numbers of the AT&T SIM card for iPad – called the integrated circuit card identification (ICC-ID) – and repeatedly queried an AT&T web address. When a number generated by the hackers matched an actual ICC-ID, the authentication page log-in screen was returned to the hackers with the email address associated with the ICC-ID already populated on the log-in screen.
The hackers deliberately went to great efforts with a random program to extract possible ICC-IDs and capture customer email addresses. They then put together a list of these emails and distributed it for their own publicity.
As soon as we became aware of this situation, we took swift action to prevent any further unauthorized exposure of customer email addresses. Within hours, AT&T disabled the mechanism that automatically populated the email address. Now, the authentication page log-in screen requires the user to enter both their email address and their password.”
AT&T’s damage control has been one-part victim, two-parts minimize the impact, sprinkled with “attack the messenger” all over the top.
AT&T’s characterization of the security team that exposed the security flaw as malicious hackers brought a swift response from Goatse:
AT&T had plenty of time to inform the public before our disclosure. It was not done. Post-patch, disclosure should be immediate– within the hour. Days afterward is not acceptable.
[…] The potential for this sort of attack and the number of iPad users on the list we saw who were stewards of major public and commercial infrastructure necessitated our public disclosure. People in critical positions have a right to completely understand the scope of vulnerability immediately. Not days or weeks or months after potential intrusion.
In addition AT&T says the person responsible for this went “to great efforts”. I’ll tell you this, the finder of the AT&T email leak spent just over a single hour of labor total (not counting the time the script ran with no human intervention) to scrape the 114,000 emails. If you see this as “great efforts”, so be it.
AT&T’s mistakes just keep on coming, ranging from ongoing billing errors amounting to hundreds of dollars to threatening customers with cease and desist orders just for e-mailing concerns to the company.
[flv width=”640″ height=”500″]http://www.phillipdampier.com/video/Bloomberg Goatse Owens Calls ATT Security Flaw Egregious 6-10-10.flv[/flv]
Bloomberg News ran this interview with a representative from Goatse Security that got a bit over-technical for the average Bloomberg viewer. (4 minutes)


 Subscribe
Subscribe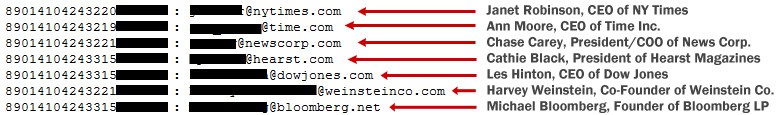

More shoddy results from exclusivity agreements
Why the hell the media keeps reporting this as “breach” or “malicious hacking”? It is security laps by AT&T and AT&T alone. AT&T as idiots deployed web application without any security audit or the audit was done by fake security specialists on public web site and by doing this they published all those e-mails to the world. And now they are blaming everyone, but them self for it. There are some reports that FBI is investigating the issue. If this is true I hope they will really take a very close look how AT&T is handling customer data and setup… Read more »
Update. There are at least one guy [1] who thinks that AT&T’s security lapse is bigger problem then AT&T admits. According to him AT&T and T-Mobile USA have been cutting corners in security for some time. There is very important key used in GSM networks it is called IMSI. If you know IMSI of the device you can own this device. By design the IMSI is not guessable based on ICCID unless you have access to the DB storing the information. This database is called HLR. But looks like AT&T (and T-Mobile USA) had made short-sighted decision to link IMSIs… Read more »